In 2015, Miller et al [1] disclosed how they were able to attack a Jeep Chrysler remotely over mobile network, and were able to fully control the car, including sending CAN messages. As a result of this Fiat Chrysler Automobiles (FCA) had to do a recall 1.4 million vehicles.
They attack allowed them to remotely send CAN messages, and control breaks, steering wheel, wipers, etc. The attack started through via an open port (6667) in the Open Multimedia Application Platform (OMAP), then to inject malicious code into the V850 ECU via SPI. As a result, they could control the entire car.
Let’s analyze this specific attack vector, using the just published version of the ISO 21434, a standardization effort that started just one year after the disclosure of this attack.
Even though they were two experts, I choose to only detail 1 expert, they didn’t need any specific knowledge about the car, the window of opportunity was unlimited, but they had to buy specialized equipment, which is an onboard diagnostics tool ($7K), in order to reverse engineer the checksum algorithm.
I guesstimated the elapsed time to make the attack, as only bits and pieces was revealed in the Blackhat video [2], where they mentioned it took 3.5 months to just read the datasheet and reverse engineer the code of the Renesas V850 MCU, and based on the other steps of the identification phase, we are reaching more than 6 months.
If we put this in the calculation, using the published version of ISO 21434:2021, we see that the attack rating is 29, which results in an attack feasibility of “Very Low”
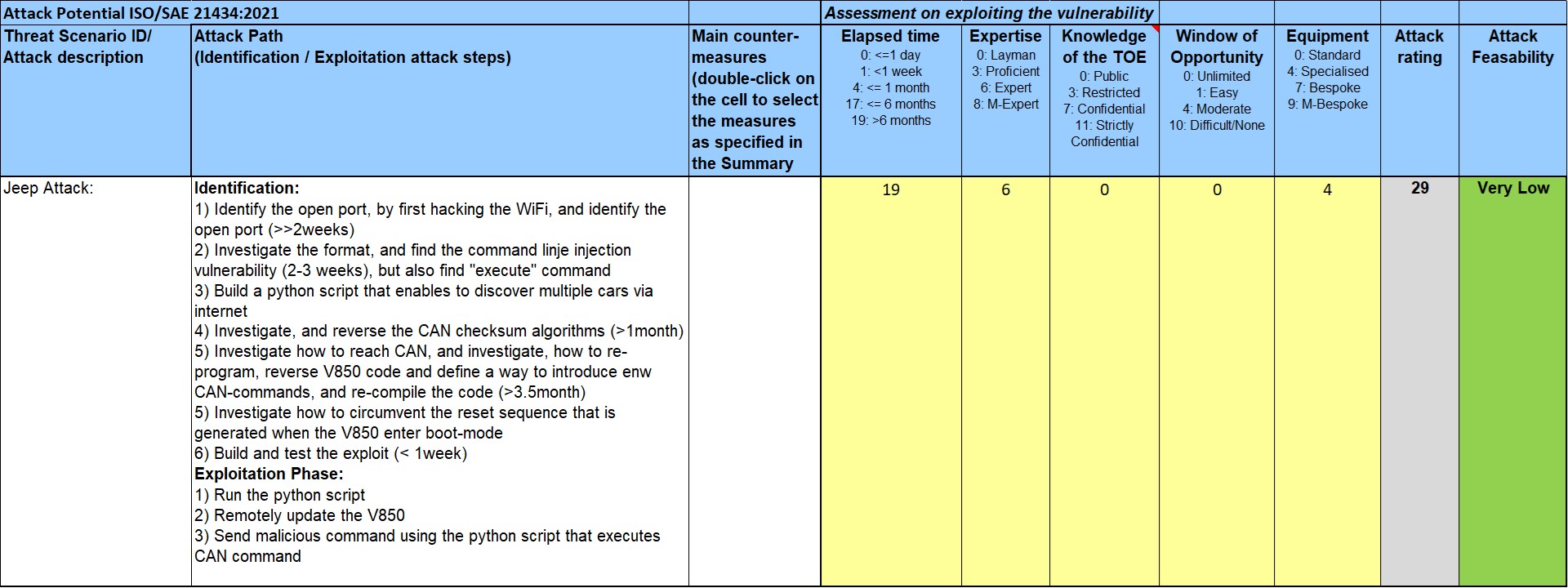
Interestingly, the full attack, as disclosed and analyzed using Attack Potential, could well be missed by OEM even today, as the Attack Feasibility is “Very Low”, and result Risk Value is “2”, as the Impact to be Severe (S:4). A subset of the attack path, that would only attack the OMAP, would certainly be spotted and would remove the vulnerability entirely, as the OEM and TIER-1 supplier is obliged to conform to ISO 21434 in EU for new vehicles introduced in July-2022 and onwards, and if implemented correctly, it will add cyber-security consistenly to the full supply chain.
It’s unlikely that we will see such obvious security holes in the future, but as the complexity grows, and with more and more V2X communication and more complex driving systems, it’s a safe bet that we will see new attacks in the future, as attack surface and complexity increases.
To remain safe in an ever-increasing automotive complexity, it’s necessary for the OEM to identify and allocate cyber-activities to entry-points, and one way to do that is to assign Cyber Assurance Level (CAL) to critical items, interfaces, and trust boundaries. It also allows the department to allocate budget for cyber-security activities during development, that could include external reviews and penetration testing. Most important, is to ensure that cyber-experts are involved, that can assist the architects in the cyber-security related activities. CAL is optional in ISO21434, but could be a tool to assist to pin-point where to invest more in cyber-security activities.
References:
[1] Miller, Valasesk: Remote Exploitation of an Unaltered Passenger Vehicle, August 10, 2015 (http://illmatics.com/Remote%20Car%20Hacking.pdf, accessed Sept-11, 2021)
[2] https://www.youtube.com/watch?v=MAcHkASmXEc
[3] ISO/SAE 21434: 2021 – Road vehicles — Cybersecurity engineering