When doing the attack feasibility rating, as defined in ISO/SAE 21434, the options are to either use CVSS, Attack Potential, or Attack Vector. The CVSS and Attack Potential are both adopted for the automotive industry, and differs from what you might have seen in the past.
These three methods differs in the way they rate feasibility, where the resulting rating may differ substantially.
It’s clear and logically that from the standardization work, remote attacks are those attacks that have the main priority, as physical attacks are generally much more difficult to achieve. They are also not systemic in the same manner as a remote attack may be. However, impact on a physical attack may have large financial and reputational damage.
For physical attacks, from what we have seen in the past is that CVSS sometimes generate a lower feasibility rating, compared to attack potential.
Let’s estimate the following Attack Path: A side-channel attack, where an expert attacker needs 5 months to extract the firmware or keys from an ECU or TCU module, requiring specialised equipments.
Let’s now calculate the attack feasbility for both Attack Potential and CVSS:
Attack Potential:
- Expert requiring 5 months of effort (Identification + Exploitation)
- The attacker has easy access to target
- Access to public documentation
- Bespoke equipment
- ”AttackPotential:/TIME:4/EXPE:6/KNOW:0/OPPO:1/EQUI:7 = 18”
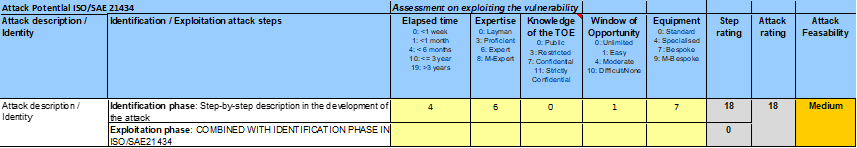
By using a simple excel-sheet, we can calculate the attack rating to 18, which is then translated to a ”Medium” attack feasibility, as defined in Annex I of ISO/SAE 21434.
CVSS
By using the same Attack Path, we estimate the Attack Feasibility using CVSS
- Access Vector: Physical (P)
- Attack Complexity: High (H)
- Privileges Required: None (N)
- User Interaction: None (N)
- AUTO-CVSS:3.1/AV:P/AC:H/UI:N/PR:N = 0.5

As we see the table above, the CVSS score is 0.5, which is then translated to Attack Feasibility Rating of ”Very Low”. Please note that that ISO/SAE 21434 CVSS scoring does not correspond to traditional CVSS.
For the same Attack Path, the Attack Feasibility Rating differes with 2 steps, where it is “Medium” for Attack Potential, and “Very Low” for CVSS.
The conclusion is that it is important to select the correct attack feasibility rating methodology for your attack paths.
Based on my own experience, I would say that the attack potential in this example is more accurate, especially for high-assurance assets, such as cryptographic keys.
Here are a few takeaways:
- For high-impact assets or high-assurance items, a senior cyber-security expert should assist the teams to assess the attack feasibility
- The security assessor should be aware of the limitations of CVSS for physical attacks

