In the previous post we talked about the difficulty of rating attack paths.
In this post, we re-use the same attack path, but looks on how tools and exploitation affects attack feasibility ratings over time.
Once a attack tool has been developed for a vulnerability, the Attack Feasibility Rating may dramatically change.
Side channel attacks is a field that have evolved quickly the last years, you can today buy a side-channel tool for <100$, freely available online with guidance on how to use these tools. This means that the Expertise drops and Equipment also gets easier/cheaper to acquire. Once the Identification of an attack path has been completed, Elapsed Time and even Knowledge of the TOE may decrease as well.
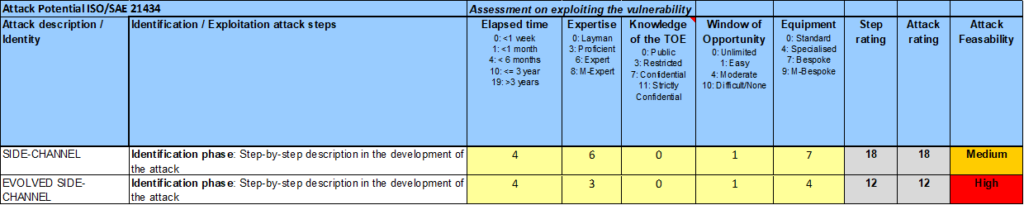
By looking at the picture below, we first see the current side-channel attack from the previous post with an attack rating of 18.
In our evolved scenario, the Expertise drops from Expert to Proficient, as we can make use of documentation and guidance available on the internet. Equipment goes from Bespoke to Specialised, as we can purchase such equipment on the internet. Such scenario is shown on the second line, where the attack potential goes down to 12 (High), resulting in an Attack Feasibility Rating of ”High”.
If we look at CVSS for the same attack, attack complexity on the evolved case changes (to low), but the Attack Feasibility Rating remains at ”Very Low” (CVSS=0.9).
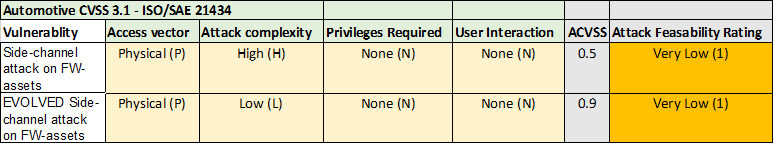
In summary, it means that we have 3 steps in difference between the evolved attack (High vs Very Low). For an organization this may cause issues both ways, either the organization over-spend money on cyber-security assurance, or the organization may end up with vulnerabilities in the field, that can be hard to mitigate in the field.
These two blog-posts demonstrates that there is a discrepancy between the methodologies, which needs to be taken into account. Maybe the ISO/SAE 21434 standardization group will refine this in upcoming revisions of the standards.
Cyber-security takes expertise and experience to understand and master.

